Click here to get the source code
Type confusion bug can be very powerful, with the potential to form the basis of 100% reliable exploits (as per Google Project Zero), more information available in What is good memory corruption
According to Common Weakness Enumeration (CWE) The program allocates or initializes a resource such as a pointer, object, or variable using one type, but it later accesses that resource using a type that is incompatible with the original type. When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access.
While this weakness is frequently associated with unions when parsing data with many different embedded object types in C, it can be present in any application that can interpret the same variable or memory location in multiple ways.
This weakness is not unique to C and C++. For example, errors in PHP applications can be triggered by providing array parameters when scalars are expected, or vice versa. Languages such as Perl, which perform automatic conversion of a variable of one type when it is accessed as if it were another type, can also contain these issues. More information about this bug in Hack All the things
We will used Hack Sys Extreme Vulnerable Driver as a demo for exploitation this bug, you can download vulnerable driver from here HackSysExtremeVulnerableDriver
Follow below links for Setting up lab:
Starting with Windows Kernel Exploitation Part-1 Setting up the Lab
Starting with Windows Kernel Exploitation Part-2
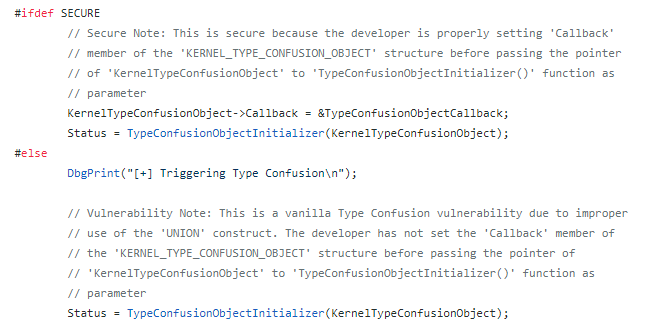
As per below code, the #ifdef SECURE block is properly setting 'Callback' member of the structure before passing the pointer to function as parameter whereas #else block does not do so and it leads to vanilla type confusion vulnerability
Device Input and Output Control (IOCTL)
The DeviceIoControl function provides a device input and output control (IOCTL) interface through which an application can communicate directly with a device driver. The DeviceIoControl function is a general-purpose interface that can send control codes to a variety of devices. Each control code represents an operation for the driver to perform.Click here to get more information
Since the driver is open source, you can find IOCTL code in mentioned link, if source code is not available we need to perform reverse engineer on the driver to get the IOCTL code to trigger the bug.
For type confusion vulnerability, we have IOCTL code as per below
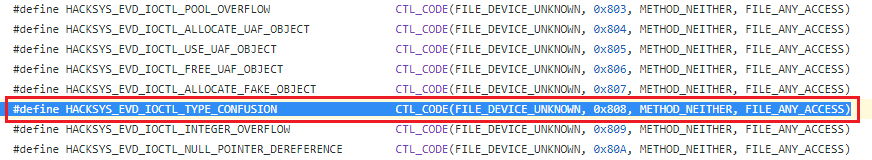
Let's decode IOCTL manually
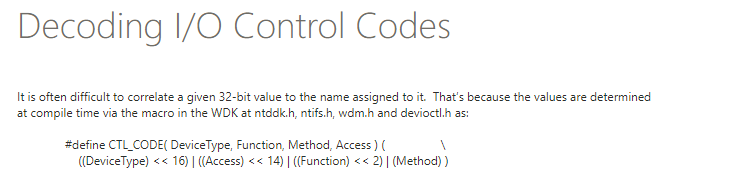
FILE_DEVICE_UNKNOWN = 0x00000022
FILE_ANY_ACCESS = 0x00000000
METHOD_NEITHER = 0x00000003
FUNCTION = 0x808
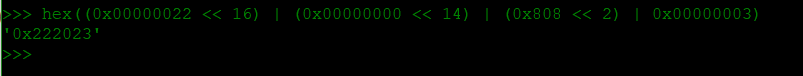
Python code for decode the I/O control codes: hex((0x00000022 << 16) | (0x00000000 << 14) | (0x808 << 2) | 0x00000003)
IOCTL code action in IDA Pro:

Exploitation is very simple, lets jump to write a python code to trigger the bug:
Download the below source code from here
Vulnerability trigger as shown below:
If we put Shellcode Address in ObjectType, it will execute perfectly. Below is a python code:
Token stealing payload was taken from: here
Download the below source code from here
Execute, the above code and you will see the magic:
Code executed in system level privilege as shown in image
Reference:
https://googleprojectzero.blogspot.ae/2015/06/what-is-good-memory-corruption.html.
https://cwe.mitre.org/data/definitions/843.html
http://howto.hackallthethings.com/2016/07/secure-c-103.html.
https://github.com/hacksysteam/HackSysExtremeVulnerableDriver
https://hshrzd.wordpress.com/2017/05/28/starting-with-windows-kernel-exploitation-part-1-setting-up-the-lab/
https://hshrzd.wordpress.com/2017/06/05/starting-with-windows-kernel-exploitation-part-2/
https://msdn.microsoft.com/en-us/library/windows/desktop/aa363219(v=vs.85).aspx
https://github.com/FuzzySecurity/HackSysTeam-PSKernelPwn/blob/master/Kernel_TypeConfusion.ps1
https://osandamalith.com/2017/04/05/windows-kernel-exploitation-stack-overflow/
https://nebelwelt.net/publications/files/16CCS2.pdf